This bug was submitted to ImmuneFi in May 2022 and was ultimately rewarded a $30k bounty despite $40M funds in risk.
INTRODUCTION
The drastic price change in LUNA revealed vulnerabilities in Perpetual systems such as Perp v1 and Drift Protocol. In the postmortem, Drift developers found a bug where an attacker could intentionally drain their entire insurance vault + user funds ($11.75M at the time).
Found here: https://driftprotocol.medium.com/drift-protocol-technical-incident-report-2022-05-11-eedea078b6d4
Quick summary:
- Attacker opens 2 accounts
- Opens a 20x long on Account 1 and a 20x long on Account 2
- Exits the 20x long on Account 1 at a far higher price than Entry price due to the price manipulation via Account 2.
The attacker ends up with massive profits while Account 2 has a massively negative account balance.
How Perpetual Protocol is Different
Drift’s exploit does not work on Perp V2 is because:
- 1% price impact limit. This means that the step where the attacker closes their entire “Account 1” long in 1 transaction does not work.
- Perp uses Uniswap v3 style LP rather than automated vAMM LP. The Drift vulnerability depends on the protocol automatically providing for Account 1 to exit their position. In contrast, V2 liquidity providers are unlikely to provide deep liquidity so far away from the mark price.
We have designed a new attack which works on Perp v2 which takes advantage of leveraged+concentrated liquidity. The exploit is similar in that it engineers a situation where one account suffers massive levered losses which is offloaded to the insurance fund/innocent users, while another account can withdraw with massive profits.
How the Exploit Works
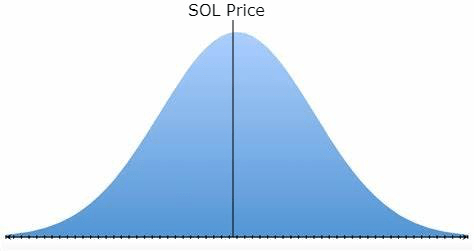
*Diagram 1 shows initial state of SOL-PERP. Blue curve represents hypothetical liquidity distribution *
- Deposit 500K into Account 1. Open longs on SOL-PERP pool with 1% price impact increments until we have a $5M USD worth of long-SOL (Diagram 2)
Lets say we get an average price of $70 SOL. Account 1 is now long 71K SOL. The mark price for SOL-PERP is now $100.5
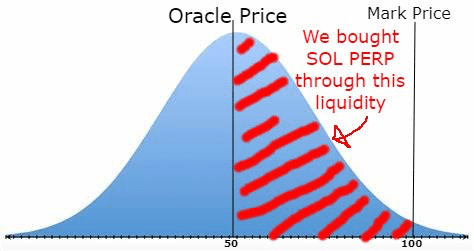
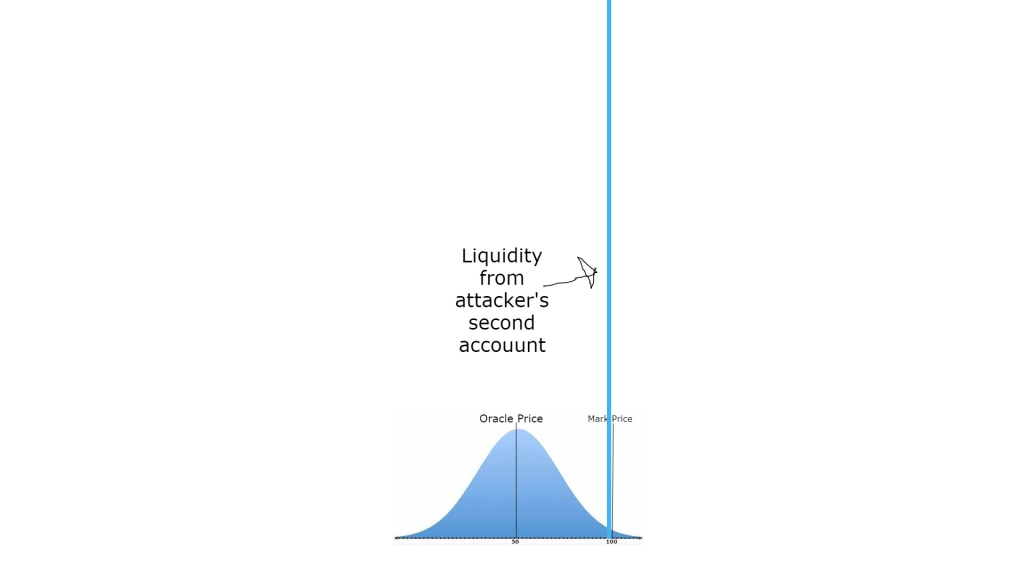
- On Account 2 deposit 710K and open a 7.1M leveraged liquidity position in a single tick around $100 – just below the Mark Price. (Diagram 3)
3.On Account 1 close your 71K SOL long at a price of $100. $2.1M. As Account 2 has a 7.1M of liquidity at the $100 price, we can exit our entire position with basically negligible price impact
- Withdraw 2.6M from Account 1.
After Step 3:
ACCOUNT 1: $2.6M Account Balance
ACCOUNT 2: ~710K collateral. 76K Impermanant SOL Short at avg entry price of $100. ($7.1M notional short)
Note that the Balance of Account 1 is higher than the total collateral initially deposited across the two accounts. Account 2 has a SOL short which was entered at $100 instead of the $50 oracle price. The “fair value” of this position -3.55M which is greater loss than the 710K in collateral.
Damage Extent:
In this example, this attacker will abandon the 710K on Account 2 as he cannot exit his position without liquidation. He withdrew 2.6M on Account 1 while depositiong only 1.21M (500K+710K) so makes a profit of $1.39M. By adjusting the numbers, the attacker could drain the entire insurance vault/collateral/clearing house.
Nuances:
- The numbers above are examples, not exact calcultions. Cannot give exact figures of how much a $X buy has Y% in price impact as it is dependent on the underlying liquidity pool which is constantly changing. We can execute this attack on any pool but need to adjust the numbers based on the liquidity.
- Due to Perp v2 limiting price impact, the attacker needs to accumulate his initial $5M long position with separate orders. Arbitrageurs could disrupt this process by opening shorts which drive the perp price back to the oracle price. In practice, arbitrageurs would run out of capital as they wouldn’t be willing to open $5M short a perp especially when there is no way to exit this position without massive slippage.
- Report neglects the 0.1% fee on opening/closing positions, but this has a negligible impact on the viability+profitability of the attack.
Recommendations
Popular orderbook exchanges like FTX restrict actions with large oracle price deviations (>10%). Perp v2 can implement these measure without impacting normal trading activity. There needs to be restrictions to liquidity provided or trades performed at large oracle price deviations. Single tick liquidity positions can act as limit orders, and this opens creative vectors of attack.
Leave a comment